Process of the Month – Scope Verification Process

You need a vigorous build process in place to ensure that agents are configured on devices PRIOR to going live on a network
Donald Rumsfeld once made a speech concerning “known-knowns, known-unknowns and unknown unknowns” (what a star!) The scope verification process seeks to find out those known-unknowns. Any devices coming onto the network and within the scope of your SAM Framework should have the capacity to be audited (be it via a dedicated agent, or through capture of data from a deployment/inventory system such as SCCM, LANDesk, etc.) The best way to address this would be through having rigorous build processes in place to ensure that agents are configured on devices PRIOR to going live on a network, but some devices do sneak through. Equally, Mergers and Acquisitions can produce widen the scope of your SAM Framework at an exponential rate – and this process could help identify those devices that you are expected to monitor for Software Asset Management purposes.
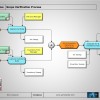
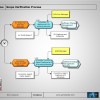
Scope Verification Process
Primary Objective
- To validate and rectify the shortfall in capturing inventory data within the scope of the SAM Framework
Secondary Objectives
- To ensure that all devices in scope have the corporate anti-virus agent installed.
- To ensure that all devices in scope have an inventory agent installed (if that is the preferred method of inventory capture)
Assumptions
- That a corporate Anti-Virus system matches/exceeds the SAM scope
- That a corporate Anti-Virus system can retrieve hardware data to enable a comparison with inventory data
- Screenshot A
- Screenshot B
Function Step Overview
| 1.10 | Subject to both assumptions being met, the Info Sec Manager conducts a trawl for all known devices that the Anti-Virus system covers. The Info Sec Manager then relays that data to the SAM Manager. |
| 1.20 | The Inventory Tool Manager also conducts an inventory sweep of all devices in the SAM Framework scope. The inventory Tool Manager then relays that information to the SAM Manager. |
1.30 |
The SAM Manager then looks to compare the Info Sec Inventory data against the device inventory data. There should be three categories any of the devices can fall into:
It’s important to choose the correct data field to compare devices against; Machine name is not recommended; nor IP address; Mac address would be the preferred option, as it is least open to corruption. |
| 1.40 | From the result generated at 1.30, the Info Sec Manager takes report No. 3 and then raises a request to have Corporate Anti-Virus software installed on those devices, which hands off to the Change Management Process. |
| 1.50 | From the results generated at 1.30 the Inventory Tool Manager takes report No. 1 and raises a request to have an inventory agent placed on those devices; which hands off to the Change Management Process. |
At least within the Change Management Process highlighted in this book; a license-check takes place to ensure that enough licenses are in place prior to deployment. A small point of order, is that if your inventory system is different from your SAM suite, then there could be consequential costs to be borne out of managing those additional systems if your SAM suite license is billed according on the number of devices it oversees.
To return to the Donald Rumsfeld quote above, the only devices you should be wondering about after having run this process are those devices that are missing both Anti-Virus software AND an inventory agent/inventory capabilities.
Other Process of the Month Articles:
- Software Re-harvesting Process
- Software Change Mangement Process
- Corporate Governance Process
- Maintain a Supported Software Catalogue
- Software Rationalisation Process
- Joiners, Movers and Leavers Process
Upcoming Process of the Month Articles:
- Named User Verification Process
- Platform Identity Process
- Software Request Process
- Software Removal Process
- Process Review Process
The process kit by Rory Canavan is available from SAMcharter.com
Can’t find what you’re looking for?
More from ITAM News & Analysis
-
Broadcom is removing expired VMware licences from its portal - take action now!
Hot on the heels of Broadcom’s announcement of the end of perpetual licences for VMware it has given customers barely a week to download any keys for licenses from its portal with expired support. This is ... -
Who Loses When Broadcom Wins?
News of a new Broadcom deal rarely arrives with great fanfare. The November 2023 VMware acquisition provoked open worry online and in business circles, with many critics wondering whether the former Hewlett-Packard spinoff’s reputation would prove ... -
Software Vendor Insights: What do the numbers tell us about the opportunities for ITAM negotiations?
What software vendor insights can be gained from the latest financial results from Amazon, Google, Broadcom, Salesforce, IBM and SAP? An important part of ITAM is paying close attention to the health of the companies we ...