NIST Cyber Security Guide for ITAM
 The USA’s National Institute of Standards & Technology (NIST) have published a Cyber Security Guide for ITAM. The publication was co-written with the National Cyber Security Centre of Excellence (NCCoE and provides an insight into what Security Professionals expect an Asset Management system to provide, and how they would go about configuring it.
The USA’s National Institute of Standards & Technology (NIST) have published a Cyber Security Guide for ITAM. The publication was co-written with the National Cyber Security Centre of Excellence (NCCoE and provides an insight into what Security Professionals expect an Asset Management system to provide, and how they would go about configuring it.
For ITAM managers working outside the Security function this publication should help you gain traction with your IT Security teams; NIST publications carry significant weight within that community.
The guide can be read at the following link https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.1800-5.pdf
There is also a web-based version here
The publication could outline a future for ITAM where you are much more closely aligned with your IT Security teams, giving you a stronger mandate and helping you deliver even more value for your organisations.
Outline
The guide concerns itself primarily with addressing the security needs of infrastructure used by large financial institutions. It starts with questions familiar to us as ITAM managers – what assets do we have, and what’s running on them? They seek to address the mis-held view that IT Asset Management is concerned with barcoding physical assets. They recognise that for the modern IT Security professional being able to answer questions such as “Which of our devices is vulnerable to NotPetya?” is of greater importance than knowing where a physical server is located.
Other challenges identified include a lack of centralised control of asset deployment and the sheer variety of devices and software deployed.
The Guide outlines the following benefits of an ITAM system:
- Discovery of device location, configuration, and ownership
- Identification of most valuable assets
- Meeting IT Audit requirements (i.e. SoX, PCI-DSS – not license compliance audits)
- Inventory vs Entitlement
- Patching
- Helpdesk response improvement
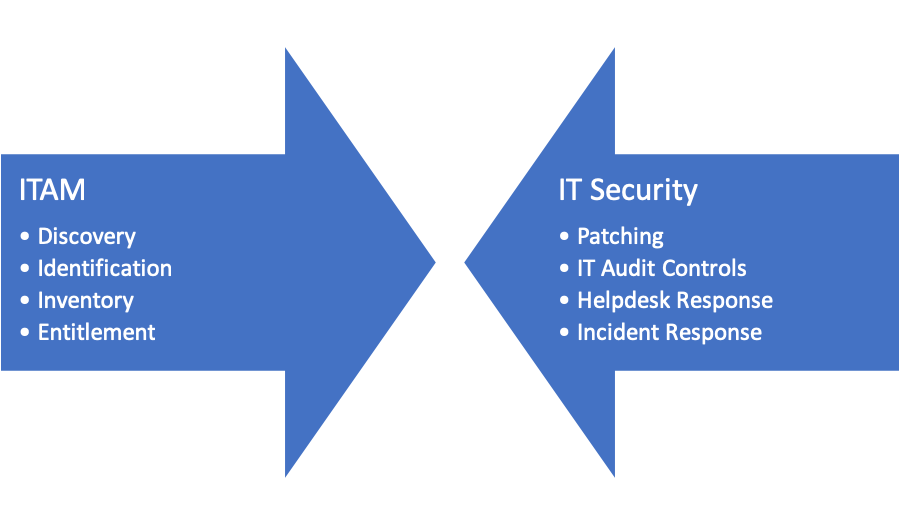 Most of these benefits closely match the benefits we as ITAM managers will have been espousing to IT Leadership teams for many years. NIST believes that;
Most of these benefits closely match the benefits we as ITAM managers will have been espousing to IT Leadership teams for many years. NIST believes that;
“ITAM enhances visibility for security analysts, which leads to better asset utilization and security.”
It also sees ITAM as
“foundational to an effective cybersecurity strategy”
These are important statements that will carry significant weight with IT Security teams and your CISO.
Where the solution differs from our traditional toolsets
Much of what is delivered by this solution is standard functionality for an ITAM tool. However, being a security standard, it is somewhat more concerned with proactive control.
As such it lists capabilities such as;
- Unauthorised Asset Discovery
- Permitted Hardware & Software controls
- Software installation restriction controls
as being important deliverables. It also recommends close integration with log analysis tools commonly used by security professionals to detect and manage cyber threats.
In order to meet these capability requirements NIST believes an ITAM solution must provide;
- Continuous monitoring and tracking of assets
- Event Auditing
- Vulnerability Scanning
- Activity Detection and Reporting
With no traditional single ITAM tool providing these capabilities NIST have adopted a multi-tool approach to deliver against the required specification. In total, 15 separate vendors and 17 tools are deployed on 7 different Operating Systems.
| Company | Product | Purpose |
| AlphaPoint (LevelBlox) | AssetCentral | Physical Datacenter Asset Management |
| RedJack | Fathom | Network Monitoring |
| Open Source | Bro | Network Monitoring |
| Open Source | Snort | Network Monitoring |
| Belarc | BelManage | Software Asset Management |
| Belarc | BelManage Analytics | SAM Reporting |
| PuppetLabs | Puppet | Network Management |
| Open Source | OpenVAS | Vulnerability Scanning |
| Splunk | Splunk Enterprise | Central Database |
| Microsoft | WSUS | Windows Patching |
| Ubuntu | Apt-Cache | Ubuntu Patching |
| Computer Associates | ITAM | Physical Asset Management |
| Open Source | OpenSwan | Secure Networking |
| Open Source | pfSense | Network Configuration |
| Tyco | iStar Edge | Physical Access Management |
| Vanguard Integrity | Security Manager | Mainframe Security Alerts |
| Microsoft | Server 2012 R2 | Certificate Management |
These together form the ITAM System
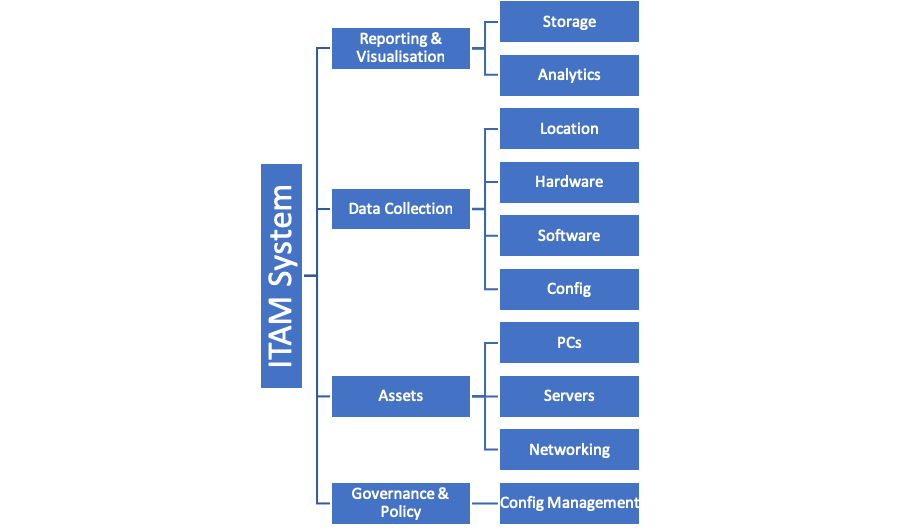 For further detail please see the following dataflow diagram
For further detail please see the following dataflow diagram
https://www.nccoe.nist.gov/publication/1800-5/_images/vol-b-image10.png
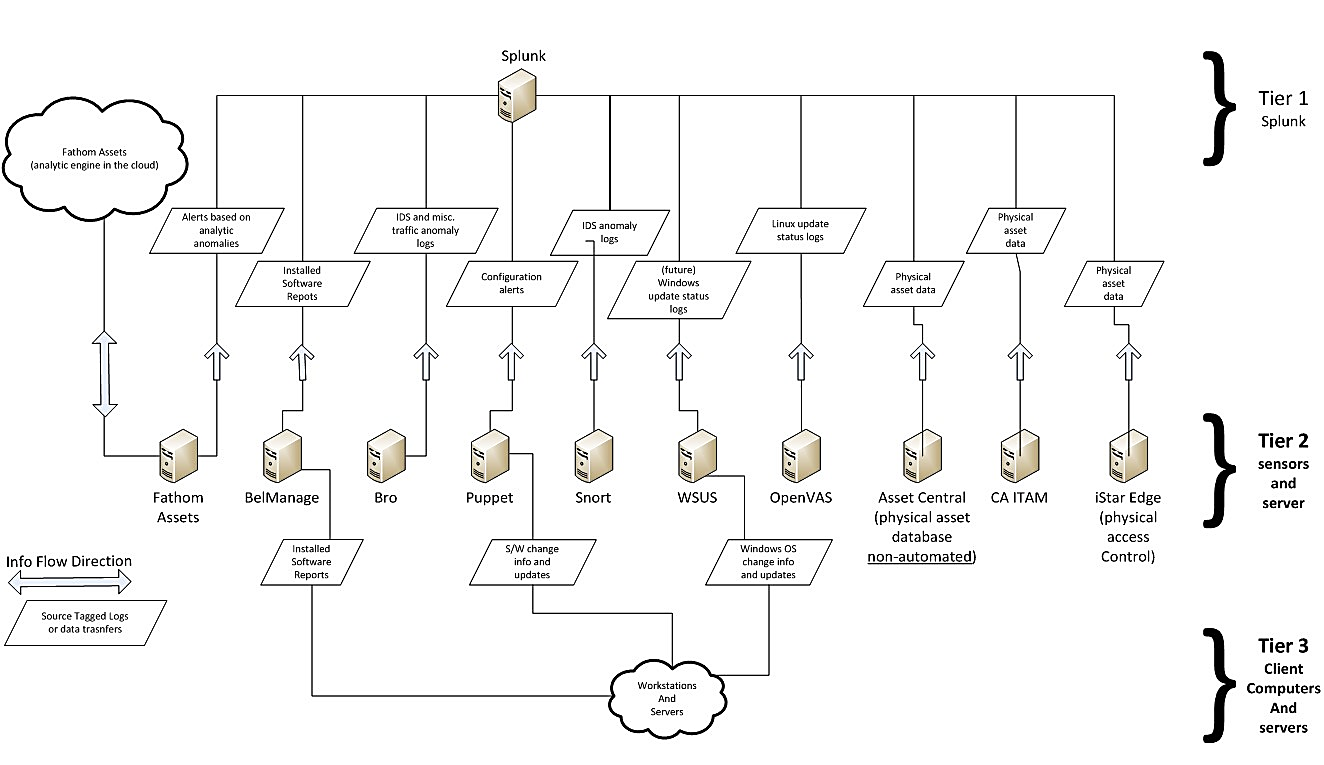
NIST ITAM Dataflow
This fearsome hydra of tools needs to inter-operate seamlessly – point-in-time exports of asset data aren’t going to cut it. The only practical means of doing this are either via API connections or by deploying middleware to provide integration and interoperability between toolsets. The standard achieves this by using many tools unfamiliar to ITAM professionals – for example, the central database is provided by Splunk (Snow’s new President, Vishal Rao, is ex-Splunk). Computer Associates (now a Broadcom division) supply physical hardware asset management capabilities. Possibly the only pure-ITAM tool that you’ll recognise is from Belarc
Setting aside the issues around keeping such a distributed system with so many moving parts working efficiently I do see the benefit of what they’re trying to achieve.
Enhanced ITAM benefits
One scenario explored is the ITAM system providing context to an intrusion detection system. In this case the analyst reviewing the anomaly is able to access full configuration details of the asset – something that isn’t usually possible with a siloed intrusion detection system.
They’ve also shown awareness in identifying the need to track VM migration. In doing so they address a typical ITAM need to ensure that virtual machine hosts are adequately licensed to run software – for example, via License Mobility rights.
The publication also provides a detailed security control mapping and reference architecture. This is important in enabling IT Security Professionals to understand where ITAM fits within their operational frameworks. IT Security, and the wider practice of IT Audit, is driven by control frameworks & NIST’s “Framework for Improving Critical Infrastructure Cybersecurity” is considered by most security professionals to be the gold standard.
What’s missing?
Technical aspects
The publication makes no mention of entitlement management or using the system to address license compliance audit risks. Whilst Belarc is listed as capable of providing entitlement information no further reference is made to how this should be used in practice. It is also notable that several of the components require manual updates and seeding, and there is extensive mention of human response to potential threats being required. Human management of security controls is subject to error and fatigue and many vendors are moving towards using machine learning and AI to address this issue.
Roles & Responsibilities
This framework is very much a technical solution. It deliberately doesn’t address policy and organisational requirements. The question therefore remains as to who should manage this system, and who is responsible for taking action on reports and analysis it produces? A clearly defined RACI is usually required by security & compliance frameworks to address this requirement. As ITAM Managers it is important that we don’t assume accountability and responsibility for deliverables we don’t directly control, and this requires careful and detailed negotiation with your IT Security colleagues. Ensure that just because this is called “ITAM” that it doesn’t become your responsibility. The level of complexity and scope that this solution attempts to manage goes way beyond our traditional responsibilities. Equally though, you need to ensure that IT Security don’t go and grab your lunch – which is why we continue to advise that you engage with your colleagues in that department. The mutual benefits are very clear.
Conclusion
A possible ITAM Future sees ITAM teams closely integrated with IT Security, Procurement, and Finance. Having the Security standards bodies recognise the importance of ITAM to their ability to deliver secure infrastructure is extremely valuable. If your Security team bases their processes, controls, and operations around the NIST frameworks you now have a common framework to deliver against. With such focus on IT Security at present this has the potential to positively influence your mandate as an ITAM Manager. Just make sure you don’t get left holding the baby!
Can’t find what you’re looking for?
More from ITAM News & Analysis
-
Broadcom is removing expired VMware licences from its portal - take action now!
Hot on the heels of Broadcom’s announcement of the end of perpetual licences for VMware it has given customers barely a week to download any keys for licenses from its portal with expired support. This is ... -
Who Loses When Broadcom Wins?
News of a new Broadcom deal rarely arrives with great fanfare. The November 2023 VMware acquisition provoked open worry online and in business circles, with many critics wondering whether the former Hewlett-Packard spinoff’s reputation would prove ... -
Software Vendor Insights: What do the numbers tell us about the opportunities for ITAM negotiations?
What software vendor insights can be gained from the latest financial results from Amazon, Google, Broadcom, Salesforce, IBM and SAP? An important part of ITAM is paying close attention to the health of the companies we ...