Mitigate risk and vulnerabilities in your organization
This article was written by Rich Gibbons, ITAM Review and Kevin Miller, Flexera.

Image by Pete Linforth from Pixabay
Chaos in the IT environment
Digital disruption is making it difficult to control IT spend for a number of reasons, including:
- IT no longer owns or may have limited visibility into some new technology investments
- Many organizations are still using manual processes and a decentralized approach to ITAM
- Lack of visibility into all IT assets leads to increased costs and higher audit risk
Even the concept of “the IT environment” keeps changing – with technologies such as IaaS and SaaS cloud, containers, and Internet of Things increasingly becoming part of an organisation’s technology stack – there are more things to manage, in more places, than ever before.
Vulnerability management
Enterprise security is more important than ever with the increasing threat of hacks and ransomware attacks. Because knowing what to protect starts with knowing what you have, SAM and ITAM can play a significant role in keeping organizations cyber-secure.
Almost half of all vulnerabilities come from software exploits, according to the Forrester Analytics Global Business Technographics® Security Survey, 2019, which puts significant pressure on the management of software assets.
The 2019 State of Vulnerability Response report from the Ponemon Institute stated that the time from a patch being disclosed to when we begin to see exploits against them are taking about 43 days; if you know your environment, this should allow for ample time to react.
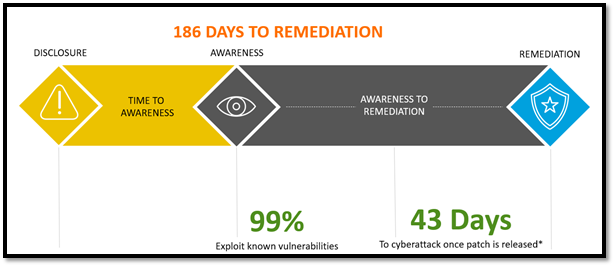
Graphic from Flexera. Cyberattack (time to exploit) updated per new information from Ponemon in 2019.
Where to start?
There are around 18,000 new vulnerabilities each year – in many ways, there are too many to comprehend which can lead to organizations taking no action. On top of that, it typically takes an organisation several hours – if not days – to package, test, and release security patches and updates. These two facts mean it’s very likely that important security patches will go un-deployed, leaving organizations vulnerable to a range of external threats. The time-gap between when vulnerabilities are disclosed, and when they are identified and fixed in applications creates a “risk window” that hackers can exploit. This risk window—also referred to as exposure time—has direct impact on whether vulnerabilities can be exploited or not, as it takes time for hackers to prepare their exploits and test them. Risk windows can lead to costly security breaches when vulnerabilities are left unpatched for long periods of time.
Having a strategy to focus in certain areas can help end the inaction and increase your security position.
Common Vulnerability Scoring System (CVSS)
CVSS is an industry standard used to communicate the severity of a security vulnerability, running from 0 (least severe) to 10 (most severe). These scores allow responders to prioritize responses and resources according to their criticality. It has long been considered best practice to focus on those vulnerabilities with a CVSS score of 7 or higher.
However, there is a new metric that organizations are leveraging to prioritize based on the likelihood a vulnerability will be exploited we refer to as Threat Intelligence. Data from Flexera’s Secunia Research tells us that only 6-10% of vulnerabilities see an actual exploit in the wild. If we look at vulnerabilities with a CVSS score of 7 or higher, we see that it only accounts for half of those that were exploited. So not considering Threat Intelligence can leave your organization focusing in the wrong areas.
Interestingly, a large percentage of the vulnerabilities exploited are in the medium severity CVSS range; between 4 and 7. This tells us that organizations cannot base priority solely on criticality. An even more basic approach is to focus on applications that are most prevalent, but top vendors only account for about 20% of exploited vulnerabilities so this too is clearly not the way to effectively manage software vulnerabilities in your environment.
It is important that you have a repeatable process that helps you manage security vulnerabilities as opposed to reacting when one hits the news and questions start coming from the top about its effect on the environment. After all, 99% of the time a vulnerability is exploited, a patch is already available. However, only 1 in 10 patches actually get deployed in a typical enterprise environment due to a lack of awareness, a lack of resources or lack of a strong process to manage software vulnerabilities. So, it is paramount that the time you spend patching is spent on the right patches as part of a strong, repeatable process.
Vulnerability Management Lifecycle
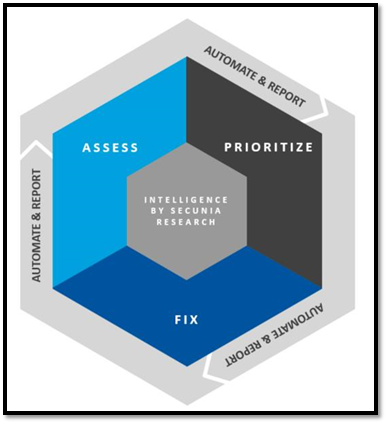
Focus on what matters to your security risk and filter out what does not. As more software vulnerabilities are discovered, it’s important that the team in charge of patching and remediation manages the process in a systematic and controlled way.
Identifying vulnerable products (including those not authorized in an organization’s environment) and pairing that with effective automated patch management is critical to reducing the risk window and eliminating the root cause of a potential exposure.
The vulnerability management lifecycle involves three key phases—assess, prioritize and fix— which include preparation, vulnerability identification, risk assessment, patch deployment, and verification (and additional re-assessment and the cycle restarts).
Addressing all steps of the vulnerability management lifecycle enables the business to strengthen the security of their network.
A Diagram for Successful Remediation

In addition to lifecycle assessment, it’s more effective and efficient to plan ahead for the management of security risks.
The diagram above shows how you can make better decisions with data. Not all of this data is always available at the outset, but with key partners like Flexera, focusing on Threat scores, criticality ratings, sensitivity of your assets to the organization and prevalence will help determine an effective course of action.
The process can start at different points in the above diagram, according to the needs of your organization as a helpful guide to how businesses can prioritize remediation efforts. Each business is different, and it is the details specific to each organization that will help to formulate the best path forward.
With that being said, many companies start with security updates and patching focused on vulnerabilities most exploited, then move on to those likely to inflict the most damage on the IT estate, follow those with attention to exploits that will infect the most sensitive assets and then concentrate efforts on applications with the widest range–those installed for the most users or on the most hardware. This provides a rounded framework toward organizational vulnerability remediation.
How ITAM can help
Risk and vulnerability management shouldn’t involve a siloed approach. While security operations are likely to handle the bulk of patching efforts, ITAM has a role in rooting out those threats through asset and data visibility:
- Know what software you have
- Know where it is
- Know when it goes end of life before it does
- Know when it still exists within your org unsupported
From IT assets to their vulnerabilities
In addition to knowing more about your vulnerabilities, maintaining your IT assets helps de-risk your organization. With reliable data that is enhanced with contextual information, you can:
- Improve access to real-time data for business initiatives
- Automatically manage license consumption to reduce waste
- Maintain continuous license compliance to minimize audit risk
- Manage contracts to reduce software maintenance and subscription costs
- Track application usage to reclaim licenses, optimize renewals and reduce denials of service
- Manage portfolio proactively to reduce cost and minimize risk exposure
While ITAM is often not directly tasked with the remediation of vulnerabilities themselves, there are key items, like end of life and support management, that can directly head off vulnerable access points for hackers before they become a liability. From employing the vulnerability management lifecycle within the organization to prioritizing efforts according to threat, criticality, prevalence and/or sensitivity, ITAM can help work strategically with their security partners to increase efficiency with effective planning.
With the right tools, processes, and even the right partner, you can gain the visibility you need to reduce manual efforts, enabling you to focus more on strategy while meeting the challenges of the changing business environment.
Further Reading
Can’t find what you’re looking for?
More from ITAM News & Analysis
-
Software Vendor Insights: What do the numbers tell us about the opportunities for ITAM negotiations?
What software vendor insights can be gained from the latest financial results from Amazon, Google, Broadcom, Salesforce, IBM and SAP? An important part of ITAM is paying close attention to the health of the companies we ... -
Flexera is first SAM tool vendor verified for Oracle E-Business Suite applications
Flexera has announced that it has been verified as the first software asset management (SAM) tool vendor for Oracle E-Business Suite applications. Almost anyone with an Oracle estate will be familiar with the company’s License Management ... -
ITAMantics - March 2024
Welcome to the March 2024 edition of ITAMantics, where George, Rich and Ryan discuss the month’s ITAM news. Up for discussion this month are. Listen to the full ITAMantics podcast above or queue it up from ...